Coal Power Generation Company Bangladesh Limited (CPGCBL), Matarbari, Cox’s Bazar Dohatec New Media successfully organized and conducted a comprehensive 5-day e-Government Procurement (e-GP) Training Program at the Matarbari 2×600 MW […]
Dhaka’s New Building Rules: How Digital Infrastructure is Reshaping Urban Governance
The foundation of any modern city is not concrete or steel—it is data. On December 11, 2025, Bangladesh took a decisive step toward that reality with the official gazette of […]
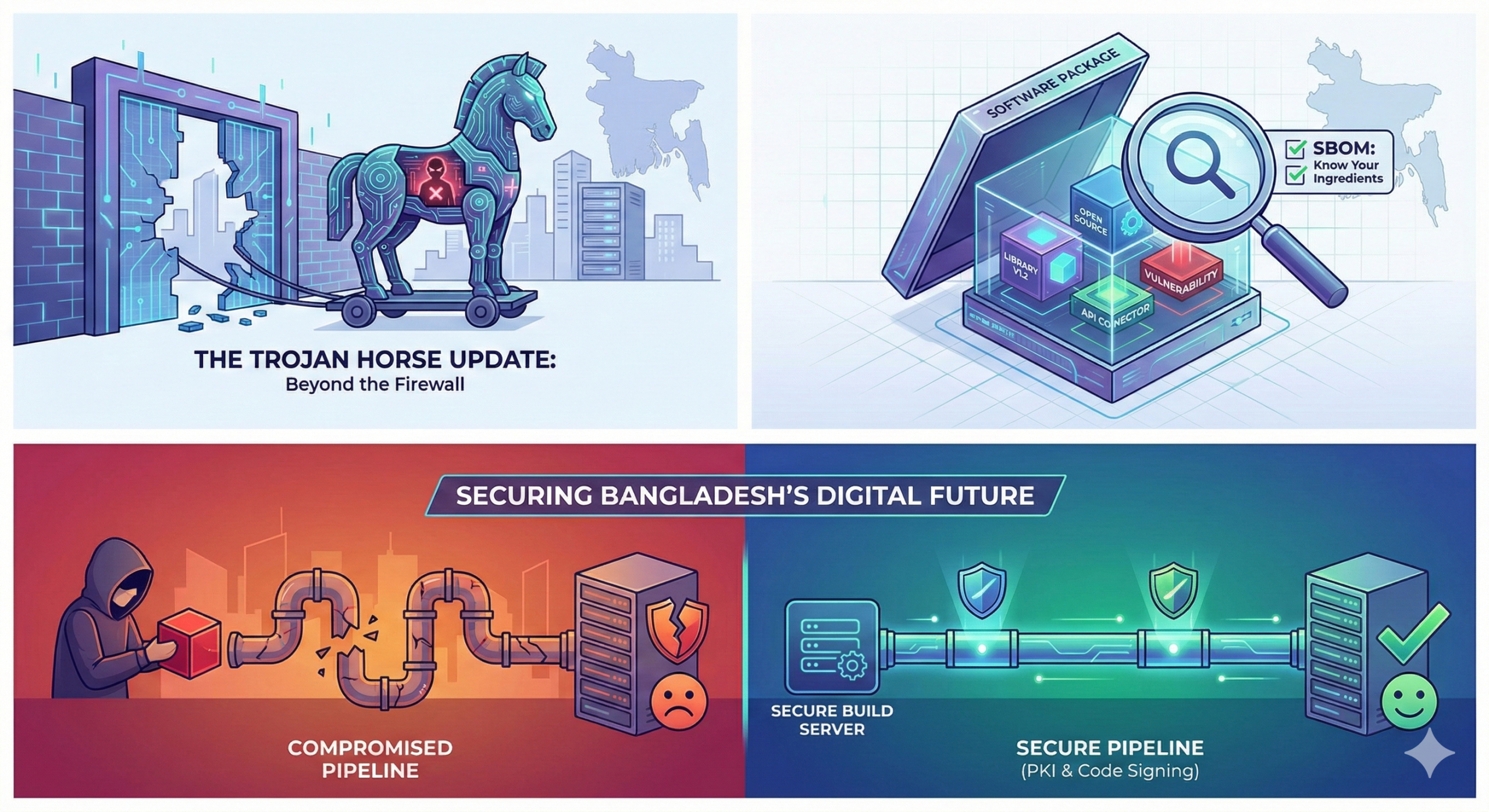
Beyond the Firewall: Why Software Supply Chain Security Matters for Bangladesh
For decades, the conventional response to cybersecurity threats in Bangladesh, as well as around the world, has been the “castle defence.” Corporations have invested significant sums in building higher walls […]
Connectivity Revolution: The Terabit Era and What It Means for Digital Infrastructure
The backbone of any digital society is its connectivity. Whether it is facilitating seamless e-Government Procurement (e-GP) or powering the next generation of AI-driven enterprise solutions, speed is the silent […]
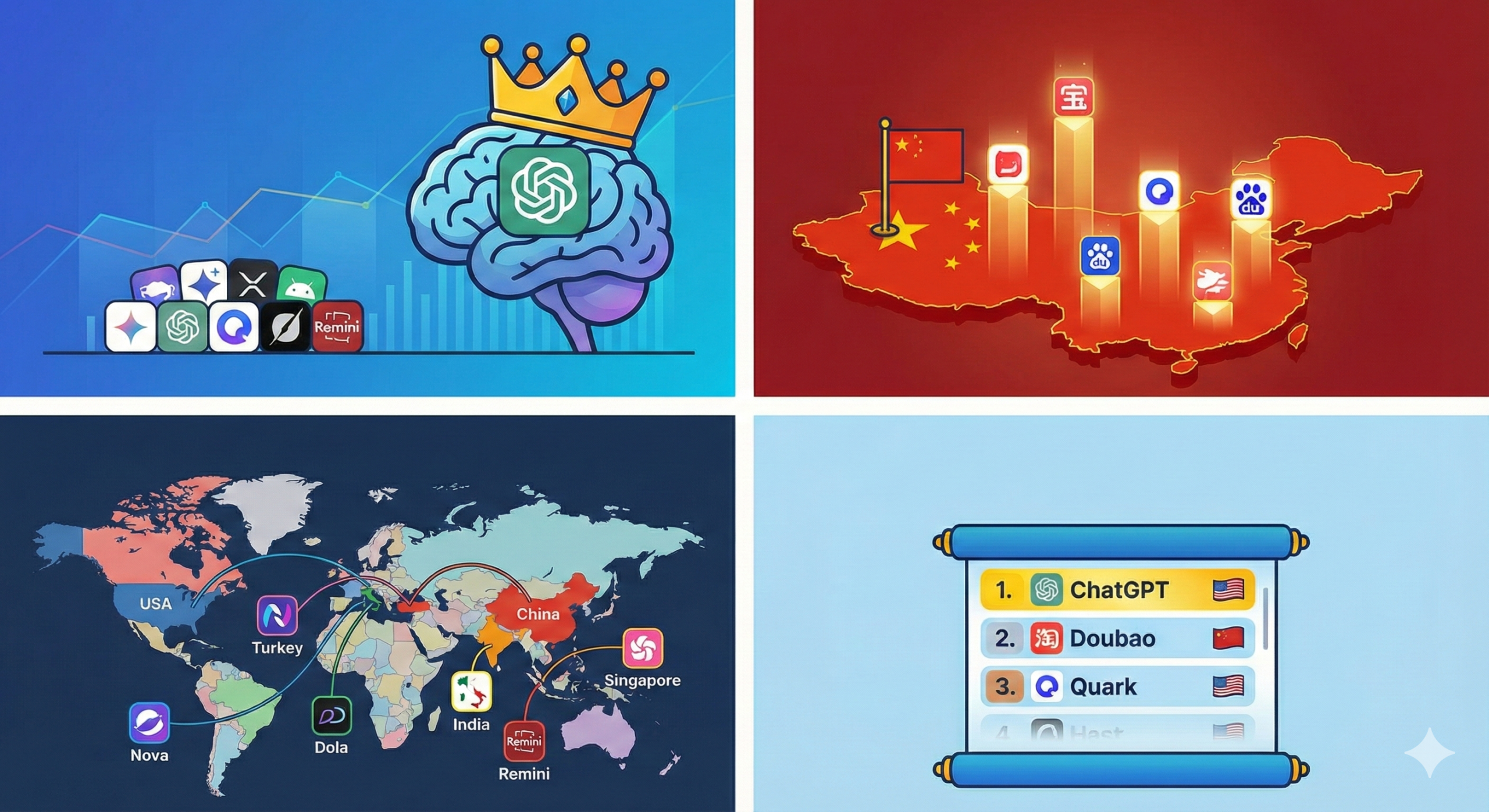
The Global AI Race: The Top 20 Most Popular Apps on October 2025
As of October 2025, Artificial Intelligence has genuinely shifted from a novelty to a daily tool. Whether it involves debugging code, composing emails, or creating surrealist art, the world is […]
Dohatec New Media at Asia PKI Consortium GA & SC Meeting and vLEI Hackathon in Hong Kong
Mr. Md Masudur Rahaman, CA Head of Dohatec New Media, proudly represented the organization at two significant international cyber security and digital trust events held in Hong Kong on 6th […]
Dohatec New Media Showcases Research on e-Government Procurement at ICITA 2025 in Oslo
Dohatec New Media proudly participated in the 19th International Conference on Information Technology and Applications (ICITA 2025) in Oslo, Norway, where its research team presented a paper titled “Factors Influencing […]
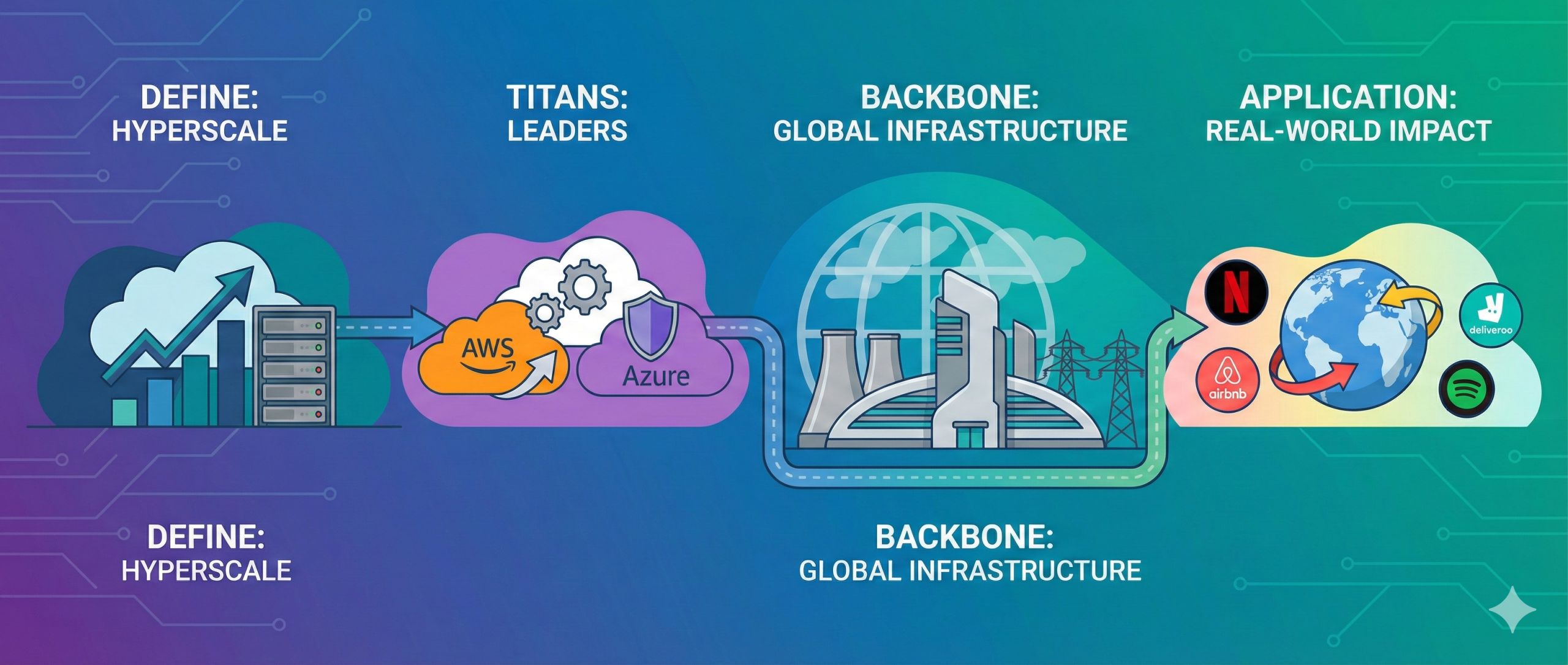
Hyperscale Cloud 101: A Guide to Mega-Scaling Business Operations
Data has become the primary asset for modern enterprises, yet managing the sheer volume of it is an increasing challenge. As workloads expand from terabytes to petabytes, traditional infrastructure often […]
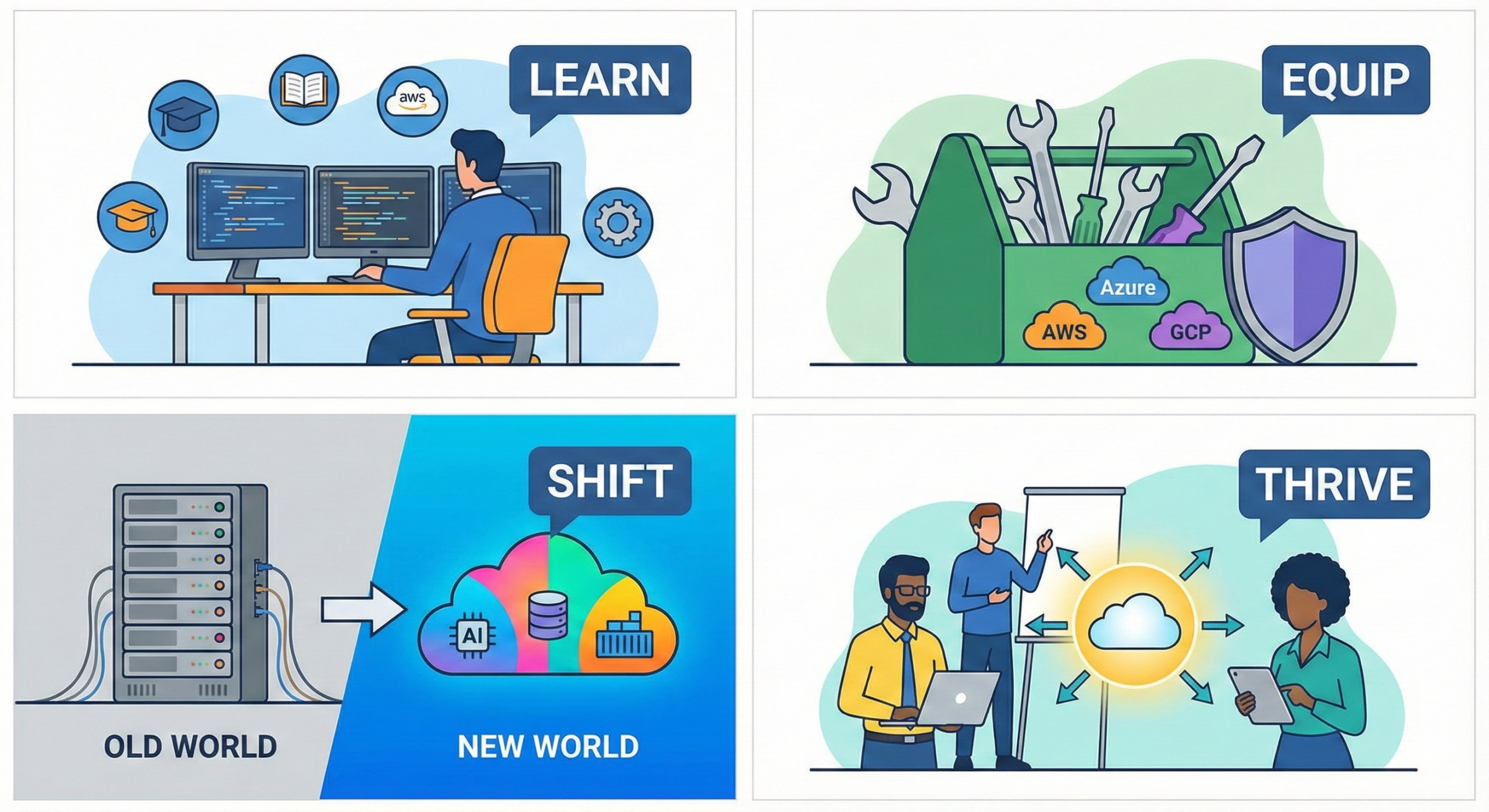
Software Pros: It’s Time to Get Equipped for the New World
For veterans of the software industry, the historical constraints are well-known: limited storage, expensive hardware, and the constant risk of physical server failure. Today, those constraints have largely evaporated, replaced […]
Leadership Visits Strengthen e-GP Training Momentum
The resumed e-GP training program received significant reinforcement through high-level leadership visits to Dohatec training centers. Mr. Md. Kamal Uddin, Secretary, IMED, Ministry of Planning and Mr. S.M. Moin Uddin […]