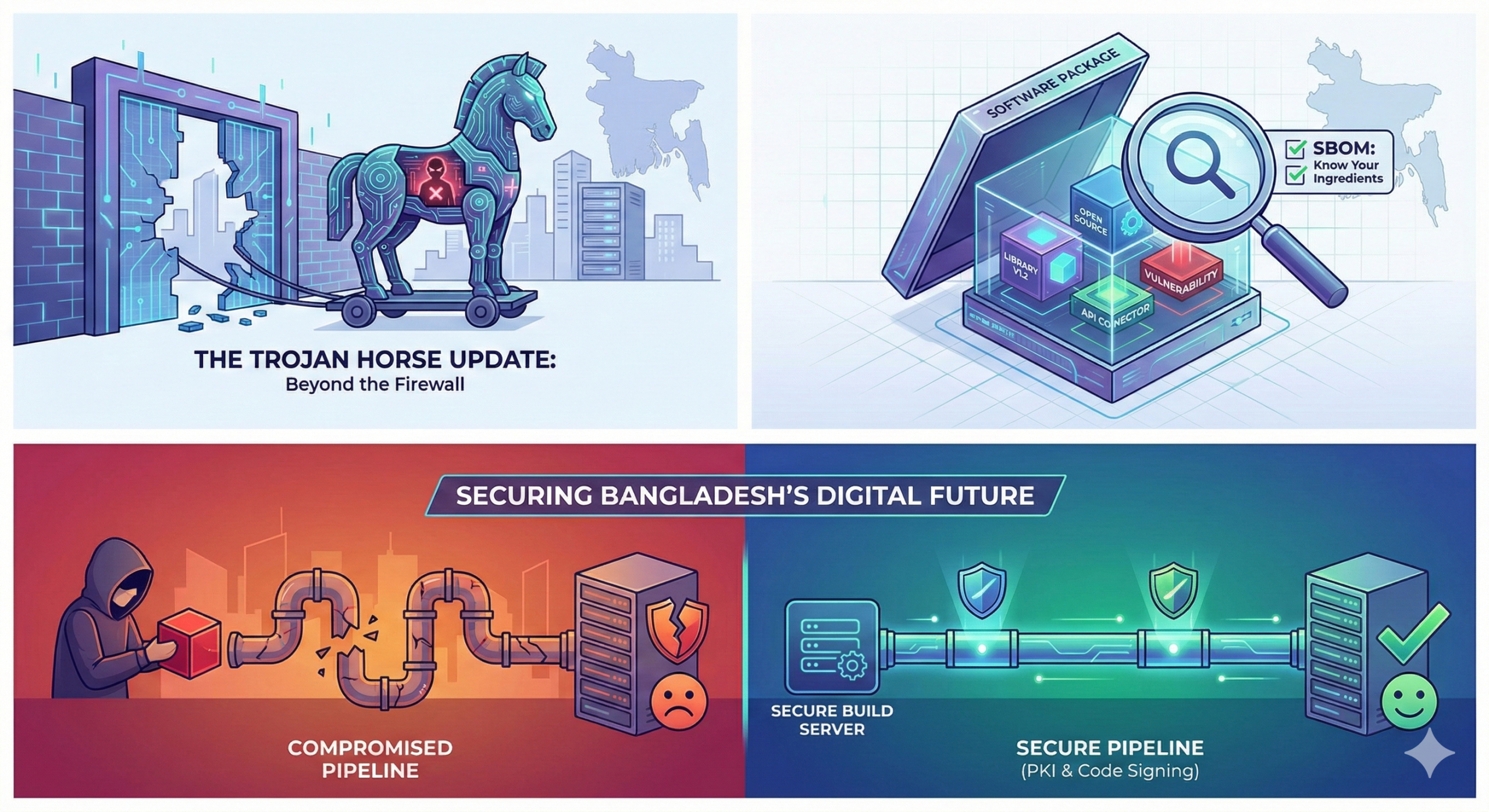
For decades, the conventional response to cybersecurity threats in Bangladesh, as well as around the world, has been the “castle defence.” Corporations have invested significant sums in building higher walls […]
Elevating Government Cybersecurity: Strategies for a Secure and Resilient Digital Future
A fundamental transformation is in progress as governments quickly digitize fundamental functions and public services to expand access and convenience to citizens. The tax filing, city utility administration, and license […]
E-Governance vs. GovTech: Decoding the Tech Revolution in Government
The rapid evolution of technology has transformed public administration, bringing e-governance and GovTech to the forefront. While often used interchangeably, these terms have distinct meanings. This blog breaks down the […]
Quantum Revolution: Securing GovTech
The emergence of quantum computing poses a major challenge to conventional cybersecurity methods. Unlike classical computers, which rely on bits, quantum computers use qubits, allowing them to solve complex problems at an exponentially faster rate. This presents a significant threat to encryption algorithms commonly employed to safeguard sensitive data. Governments need to make proactive investments in quantum-resistant cryptographic algorithms and transition to quantum-safe infrastructure to address these risks. This will help them protect crucial information and maintain a competitive advantage in the digital era.
A Framework for Privacy: Understanding Bangladesh’s Data Laws
In today’s digital age, personal data has become an invaluable asset. As individuals and organizations increasingly rely on technology, the risks associated with data breaches and unauthorized access have grown significantly. Bangladesh, like many countries, has recognized the importance of data privacy and has taken steps to strengthen its legal framework. However, challenges remain in ensuring effective implementation and enforcement.
This article explores the current state of data privacy in Bangladesh, including the key regulations and initiatives in place. It also examines the challenges faced in implementing these laws and the potential benefits of a robust data privacy framework. By understanding the importance of data protection and taking proactive measures, Bangladesh can safeguard its citizens’ rights, foster innovation, and build a more secure digital future.
Adapting and Advancing: Ethical Hacking in the Digital Age
In today’s digital landscape, where cyber threats are becoming increasingly sophisticated, ethical hacking has become a crucial component of a robust cybersecurity strategy. Ethical hackers can help organizations strengthen their defences and mitigate cyberattack risks by proactively identifying and exploiting vulnerabilities. This practice is particularly critical for governments, which often handle sensitive data that is highly valuable to malicious actors. Ethical hackers can simulate real-world attacks, allowing organizations to identify weaknesses and develop effective countermeasures, ultimately protecting critical infrastructure and national security.
Trust No One: The Zero Trust Imperative
The digital landscape is volatile, marked by escalating cyber threats. As organizations become increasingly reliant on technology for operations, the potential consequences of cyberattacks have grown exponentially. Traditional security models […]
AI & ML Power Up Security: Analyzing, Anticipating & Adapting to Threats
The digital landscape is teeming with cyber threats, demanding robust defenses. Traditional methods struggle with the vast amount of data security analysts need to sift through. AI and Machine Learning (ML) are emerging as powerful tools, empowering security teams. AI excels at analyzing large datasets, identifying hidden threats, and automating tasks. Unlike overwhelmed human analysts, AI can uncover subtle anomalies that might signal a security breach. ML algorithms continuously learn and adapt, enabling AI to stay ahead of evolving cyber threats. This proactive approach extends beyond threat detection. AI can predict potential attacks and vulnerabilities, allowing organizations to take preventive measures. However, AI isn’t a silver bullet. Cybercriminals constantly develop new tactics, and AI requires ongoing updates to maintain effectiveness. Additionally, ethical considerations regarding data privacy and bias in training data must be addressed. Overall, AI and ML are revolutionizing cybersecurity, offering a powerful line of defense in the ongoing battle against cybercrime.
The Enigmatic Pull of the Dark Web: Whispers in the Digital Underbelly
Hidden beneath the familiar internet is a mysterious realm known as the dark web. It tempts people with promises of anonymity and forbidden knowledge, drawing in a diverse group of individuals, including the curious, marginalized, and even those on the edge of legality. While the idea of freedom from censorship and access to hidden information is alluring, caution is necessary when exploring this shadowy domain.
The dark web is not just about the sensational headlines; it presents very real dangers. Its murky corners are filled with disturbing content that can warp perceptions and desensitize users to the consequences of their actions. Anonymity, which people often perceive as a shield, can embolden individuals to engage in illegal activities, blurring the lines between virtual transgression and real-world repercussions.
However, responsible exploration of the dark web is possible. Curiosity can drive a desire to learn more, but awareness is key. Recognizing the psychological risks, setting clear boundaries, and prioritizing mental well-being are crucial first steps. Understanding the legal implications and utilizing secure tools like VPNs and trusted sources further aid responsible engagement.
The dark web is a complex enigma, where the thrill of discovery can be dangerous. Approaching it with caution, knowledge, and measured curiosity allows us to navigate its depths while avoiding falling prey to its shadows. Remember, responsible exploration is not just about venturing forth, but also about returning safely, carrying the insights gleaned without succumbing to the darkness within.
Mitigating Human Error in Cybersecurity: Strategic Approaches
In today’s digital world, cybersecurity is crucial for individuals and organizations, and it requires both technological solutions and human awareness. Cognitive biases, emotional manipulation, and the lack of security awareness make humans vulnerable to cyber attacks. To address these challenges, effective security awareness training, multi-factor authentication, strong password policies, and leveraging technology solutions are essential. By understanding the psychology of cyber attacks and promoting security awareness, individuals and organizations can reduce the vulnerability of the human factor in cybersecurity. Building a secure digital world requires continuous efforts and collaboration between individuals, organizations, and security professionals.