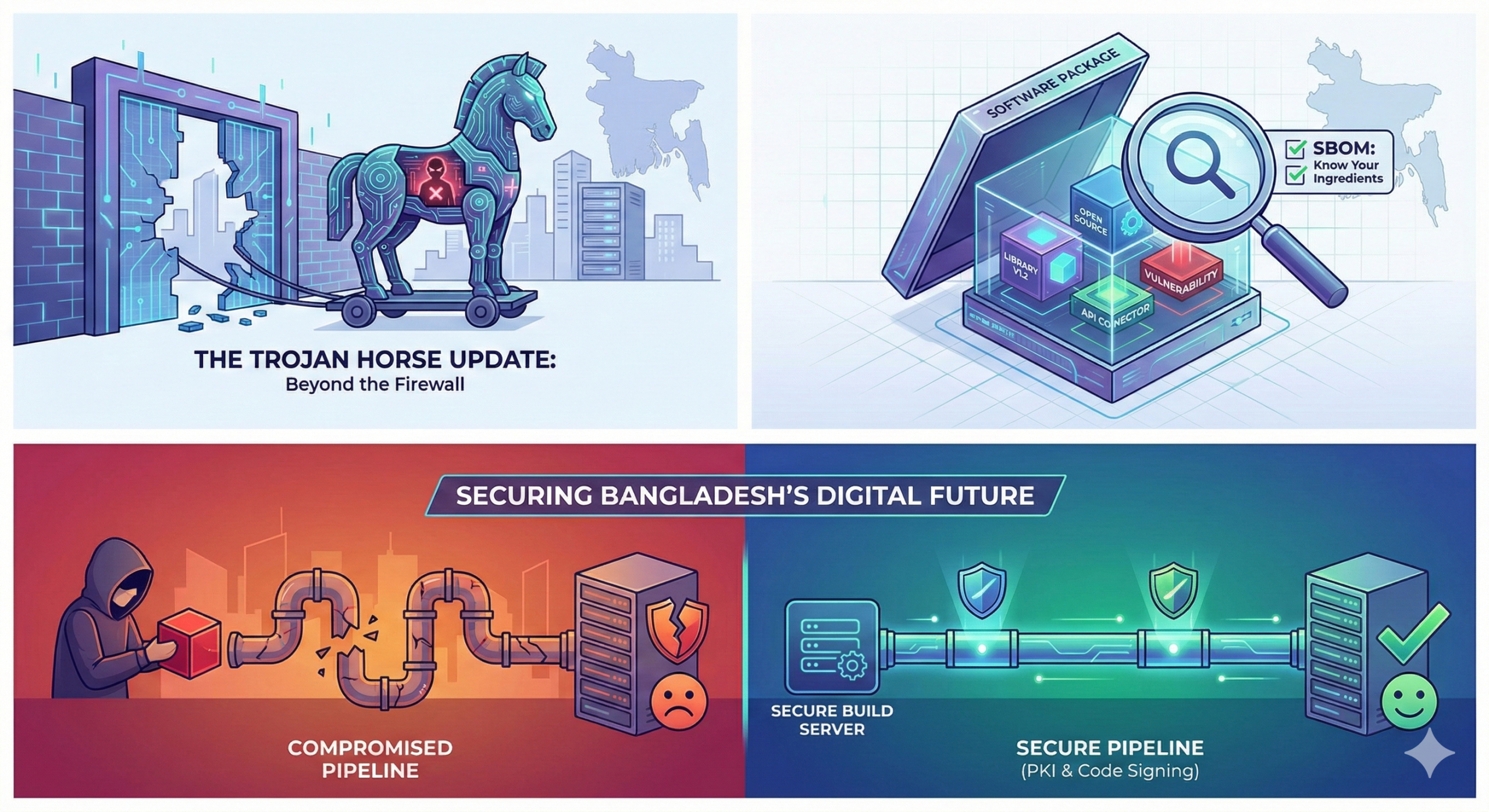
For decades, the conventional response to cybersecurity threats in Bangladesh, as well as around the world, has been the “castle defence.” Corporations have invested significant sums in building higher walls […]
Connectivity Revolution: The Terabit Era and What It Means for Digital Infrastructure
The backbone of any digital society is its connectivity. Whether it is facilitating seamless e-Government Procurement (e-GP) or powering the next generation of AI-driven enterprise solutions, speed is the silent […]
E-Governance vs. GovTech: Decoding the Tech Revolution in Government
The rapid evolution of technology has transformed public administration, bringing e-governance and GovTech to the forefront. While often used interchangeably, these terms have distinct meanings. This blog breaks down the […]
DeepSeek: Balancing Cost, Performance, and Global Ambition in AI
DeepSeek, an emerging AI startup founded in May 2023 in Hangzhou, China, is rapidly redefining the global AI landscape with its groundbreaking innovations. By training a large language model in just 55 days for under $6 million, DeepSeek challenges the notion that high-performance AI requires hefty investments, positioning itself as a strong competitor to established giants like OpenAI and Google.
With its highly successful AI assistant chatbot topping U.S. App Store charts and the release of the R1 reasoning model, DeepSeek is already reshaping industry dynamics and prompting significant stock fluctuations among major tech firms. Analysts have even dubbed this moment a “Sputnik moment,” highlighting the urgent shift in competitive power as DeepSeek underscores China’s growing influence in the global tech arena. As it continues to push boundaries, the future of AI—and the technological landscape as a whole—appears poised for a dramatic transformation.
Exploring New Frontiers: Dohatec at the 7th BMIC
The 7th BMIC in Bangkok, Thailand, provided a valuable platform for Dohatec to engage with global leaders in border management and identity solutions. The conference highlighted the importance of collaboration and the role of technology in addressing the challenges of modern border security. Dohatec gained valuable insights into emerging trends and best practices, which will inform the development of innovative solutions and contribute to a more secure and interconnected world.
Quantum Revolution: Securing GovTech
The emergence of quantum computing poses a major challenge to conventional cybersecurity methods. Unlike classical computers, which rely on bits, quantum computers use qubits, allowing them to solve complex problems at an exponentially faster rate. This presents a significant threat to encryption algorithms commonly employed to safeguard sensitive data. Governments need to make proactive investments in quantum-resistant cryptographic algorithms and transition to quantum-safe infrastructure to address these risks. This will help them protect crucial information and maintain a competitive advantage in the digital era.
Transforming Cities and Security: The Digital Twin Revolution
In today’s rapidly evolving digital landscape, governments are turning to digital twin technology to enhance infrastructure management, bolster public safety, and optimize resource allocation. By creating virtual replicas of physical assets, such as bridges, roads, and public buildings, governments can monitor real-time data, predict maintenance needs, and simulate various scenarios to improve decision-making. While digital twins offer numerous benefits, including increased efficiency and security, they also introduce new challenges that require robust strategies to protect sensitive information and critical systems.
5G: The Future of Public Services
As 5G technology continues to evolve, it presents a double-edged sword for governments. While its potential to revolutionize public services is immense, it also introduces new challenges related to security, infrastructure, and environmental impact. Striking the right balance between innovation and responsibility will be crucial in harnessing the full potential of 5G.
Global Tech Strategy: Antony Blinken’s Insight at RSA 2024
Representatives from Dohatec New Media attended the RSA Conference 2024 in San Francisco, USA where they attended a speech by The US Secretary of State, Antony Blinken. The speech highlighted […]
Adapting to AI: Reskilling for a Dynamic Future
As AI continues to revolutionize how we work, the key to success lies in a harmonious collaboration between humans and technology. This dynamic partnership opens new doors for innovation and productivity, provided that we strategically invest in reskilling and upskilling our workforce. By embracing continuous learning, focusing on critical human skills, and fostering a culture of adaptability, businesses can thrive in an era where humans and AI work side by side to create a brighter future.