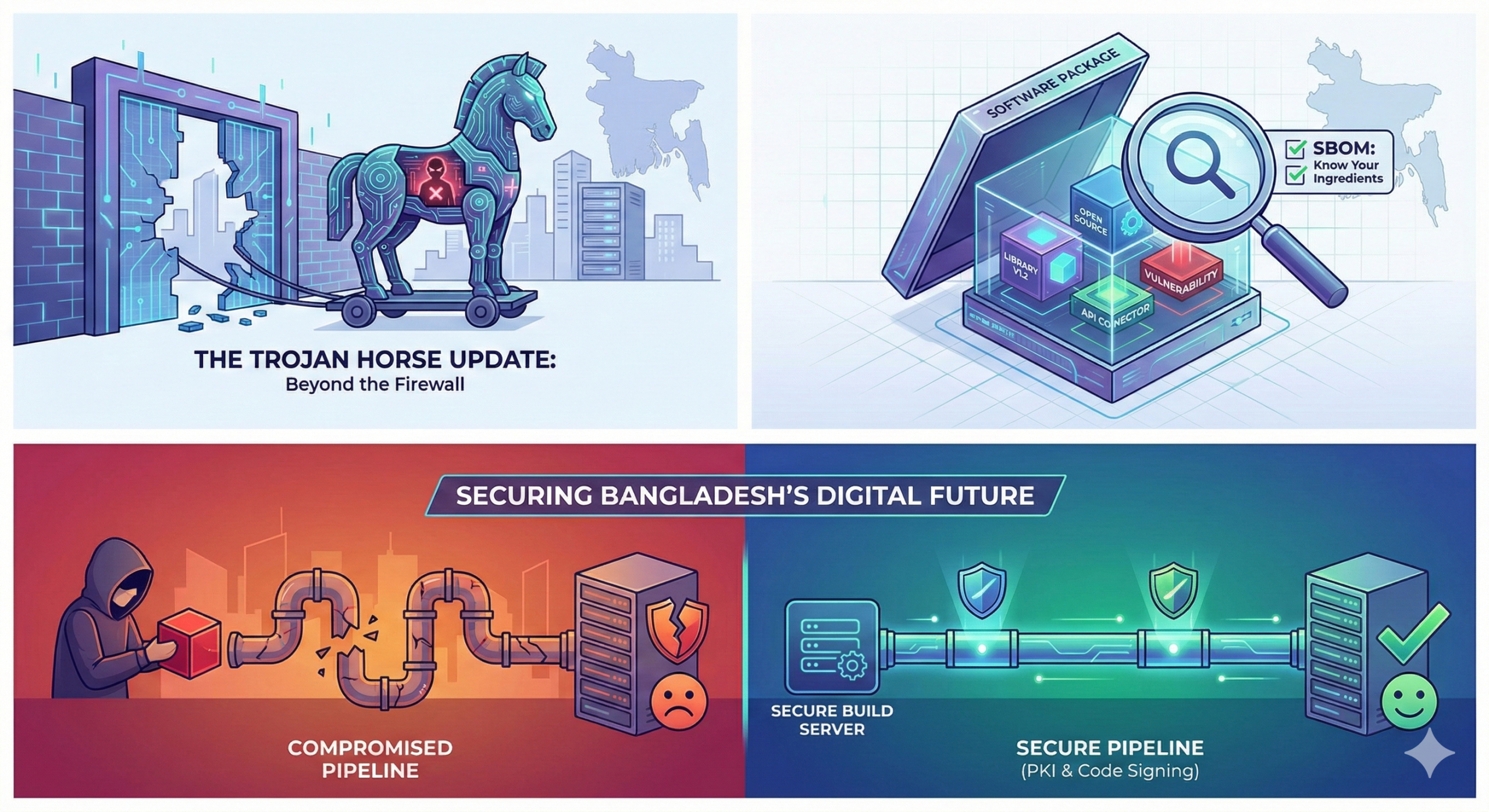
For decades, the conventional response to cybersecurity threats in Bangladesh, as well as around the world, has been the “castle defence.” Corporations have invested significant sums in building higher walls (firewalls), deeper moats (intrusion detection systems), and stronger gates (multi-factor authentication). The strategy is straightforward: the bad guy is necessarily the one who’s on the other side of the wall.
What if, however, the enemy comes to me within a sealed, trusted package?
Then, in 2020, the cybersecurity world was shocked by the SolarWinds hack. Hackers did not “break in” to the US government or the Fortune 500 in the classical sense. They hacked the supply chain. They breached the build process of a trusted supplier’s software, inserting malicious code into an update that thousands of network administrators innocently downloaded, believing it was safe because it was signed.
And this is the “Trojan Horse” of the modern era. With Bangladesh racing ahead towards the dream of a “Smart Bangladesh” through the transition of key infrastructure like government procurement (e-GP), banking, and citizen services into the cloud, we have no choice but to confront the unpleasant truth that a firewall is of no use if the software running behind it is already compromised even before the firewall is installed. It is time to look beyond the firewall and focus on software supply chain security.
What is Software Supply Chain Security?
To understand a secure supply chain, it is necessary first to demystify how current software is developed. The fact is, no software application is an island. Current software is never developed from scratch. Software is assembled. There is custom code, but also tens, if not hundreds, of dependencies.
Software Supply Chain Security is the process of protecting the entire software supply chain, from the developer’s computer through the repository, build server, and ultimately production.
The key consideration is the Software Bill of Materials (SBOM). This is like the nutrition facts box of a prepared meal. You wouldn’t eat the meal if the box didn’t include the ingredients, especially if you have a severe allergy. Likewise, the SBOM contains all the “ingredients” of a piece of software—that is, all the open-source libraries. Without an SBOM, a CTO wouldn’t be able to verify whether their most important app uses a library that was discovered to have a serious vulnerability (such as the famous Log4j vulnerability) three years ago. The risks in the supply chain are distinct from traditional hacking.
- Dependency Confusion: Attackers can upload malicious code to public repositories with names similar to internal company tools, hoping developers will accidentally install the bad version.
- Compromised CI/CD Pipelines: If the automated servers that compile and build code are compromised, an attacker can insert malware into the final product without the developer ever seeing it in the source code.
The Bangladesh Context: Fast Growth, Hidden Risks
Bangladesh is in the midst of hyper-digitization. From the growth in FinTech and Mobile Financial Services to the integration of land records and NID, the growth underway is nothing short of breathtaking.
However, during the rollout process, security is sometimes treated as secondary to functionality. This is because there is a culture of “download and deploy” in software development. This is especially true when developers face the challenge of meeting deadlines. This culture is prevalent among local software developers.
This is perhaps acceptable for an informational leaflet site. Still, it is clearly a far more serious concern for critical infrastructure services such as the e-Government Procurement (e-GP) system, which handles billions of Takas in government expenditure.
A cyberattack on Bangladesh’s digital infrastructure supply chain will not be a mere computer glitch. It will be a matter of sovereignty. What if a cybercriminal or a nation-state compromised the update process for a popular banking system or government website? This could have disastrous effects. As we construct “Smart Bangladesh,” we need to ensure we are not building our digital bricks with hollow cores.
The Anatomy of a Secure Pipeline
What does a “secure” software supply chain actually look like? This goes well beyond antivirus scanning and builds security into the code manufacturing process itself. An advanced, secure “software supply chain” has three “non-negotiable” pillars: “Identity, Hygiene, and Isolation.”
- Identity as Perimeter (Code Signing): In the physical realm, essential documents must be stamped and notarised to verify authenticity. In the virtual realm, this is accomplished by Public Key Infrastructure (PKI), or Code Signing. A secure pipeline guarantees that cryptographic keys digitally sign each line of code. This is like applying a wax seal. If any hacker or even an insider attempts to modify this line of code by as little as one byte after signing, the digital signature will fail. The operating system or server will instantly deny this update as “untrusted.” Thus, it guarantees that the software running on the client computer is mathematically equivalent to the version created by the developer at his desk.
- Automated Hygiene (DevSecOps): Humans are poor at reviewing thousands of lines of code for vulnerabilities. The code repositories use “gatekeepers.” The code must pass through these gatekeepers before it can be written. These gatekeepers will scan the code to identify vulnerabilities in third-party libraries. The automation will reject the code if it contains any vulnerabilities, indicating it uses an outdated library with a known issue.
- “Clean Room” Build Environment: Never build critical software on a developer’s own machine, which could be infected with malware or misconfigured. A clean build environment uses isolated build servers, which are essentially “clean rooms.” They are created solely for software construction and are discarded afterwards. They are not connected to the open Internet (to prevent downloading untrusted scripts) and are run under the principle of Least Privilege Access. This means even if the developer’s box is compromised, the production software stays clean.
Actionable Advice for Decision Makers
A mindset shift is required for CTOs, CIOs, and government decision-makers who will read this. This is because the new paradigm of supply chain security shifts the focus from “Is it secure?” to “How was it built?”
Here are three steps you can take now to protect your organization from supply chain attacks:
- Demand Transparency (Ask for the SBOM): When you buy software, ask your suppliers if they can supply you with a Software Bill of Materials. Even if you cannot analyse it, it demonstrates that you care about the origin of your code. A good software vendor should be able to give you details about what’s inside their “black box.”
- Authenticate Digital Signatures: Ensure your IT security policy requires verifying digital signatures for all software updates. Any update that doesn’t include the trusted vendor’s digital signature should never be installed on your network, under any circumstances. This is the best way to protect your network from the kind of attack that happened with SolarWinds.
- Review Your “Outbound” Traffic: While most firewalls are configured to block external access to your systems, your build and infrastructure servers also need protection against outbound traffic. A build server does not need to contact the entire Internet. Such traffic can be prevented to ensure that a hacked machine does not “phone home” to the hacker’s command-and-control server.
Conclusion: Trust, But Verify
As the cybersecurity community knows, there is an old Russian proverb that former President Ronald Reagan often quoted: “Trust, but verify.”
As we move boldly into the future with cloud computing and AI in Bangladesh, our need for third-party software will continue to grow. It’s an indication that we are moving in the right direction, but it also carries a greater sense of responsibility. It’s not enough that the software works. It has to be secure.
You can’t add security as an afterthought. It is actually the way that software is created. At Dohatec, we recognise that innovation matters, but it is also crucial that it be done with integrity. This is what we can accomplish by utilizing PKI, code signing, and maintaining a clean supply chain. This is what we provide to our clients: Certainty.